Businesses are using strategies like firewalls, proxy servers, and demilitarized zones (DMZ) more frequently to shield their private networks from online threats. However, not every attack originates externally. The Local Area Network (LAN) is the weakest link in the chain of network security. Once an attacker gains access to the network, there are numerous methods at their disposal for monitoring and modifying data traffic. The ARP protocols’ vulnerability is exploited by internal attackers. Administrators are faced with security issues when this is utilized with IPv4-based Ethernet networks to translate IP addresses to MAC addresses.
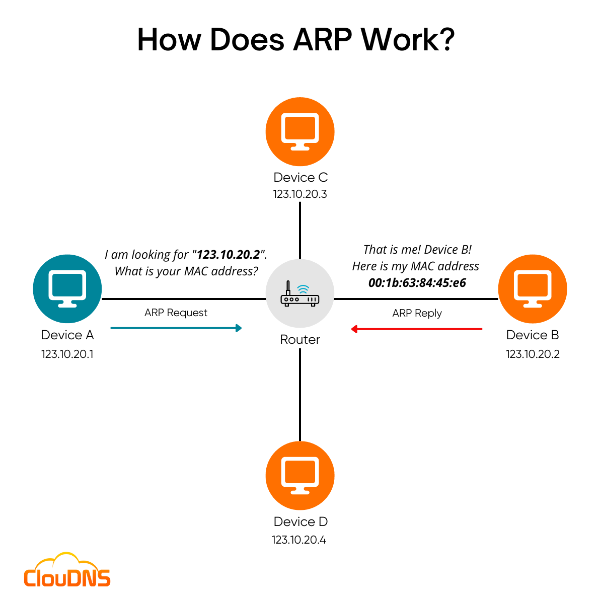
Let’s say that Device A wants to find the MAC address of Device B but only has their IP address. Device A will broadcast a message to the entire network asking who is 123.10.20.2? and what is your MAC address?? Device C and Device D will check their IP, realize it is not for them and will ignore the message. Device B however, will recognize his IP is being called, and will respond confirming that they are in fact IP 123.10.20.2, and will send their MAC address back to Device A.
Device A will then store this IP address along with it’s MAC address for future use in something called an ARP CACHE
What is an ARP CACHE?
An ARP CACHE is kind of like an address book used to store and record past connections that have been established between devices on a network. This is so the next time the devices want to make a connection through the default gateway, the addresses will be recorded and the messages will know what device to relay the message to based on memory.
What is ARP Spoofing?
ARP Poisoning is a kind of cyberattack that leverages flaws in ARP, which can be used to snoop on, reroute, or stop all traffic on a network. Often the attack is used as an opening for other attacks, such as denial of service, man in the middle, or session hijacking attacks.
How exactly does an ARP attack happen?
The basic principle behind ARP poisoning is to exploit the lack of authentication in the ARP protocol by sending spoofed ARP messages over the network. ARP attacks can done from a compromised host on the LAN, or from an attacker’s machine that is connected directly to the target LAN. Remember I said Device C and Device D both ignored Device A’s request as it was not their IP?? well.. what if one of those devices pretended it was theirs? ARP spoofing is the act of an attacker masking their IP to *look like* the IP that is being called for by device A, allowing the hackers machine to not only be authenticated in the ARP cache, but now the hacker is able to intercept all traffic as a man in the middle between the targets computer and the default gateway on the router.
Demonstration
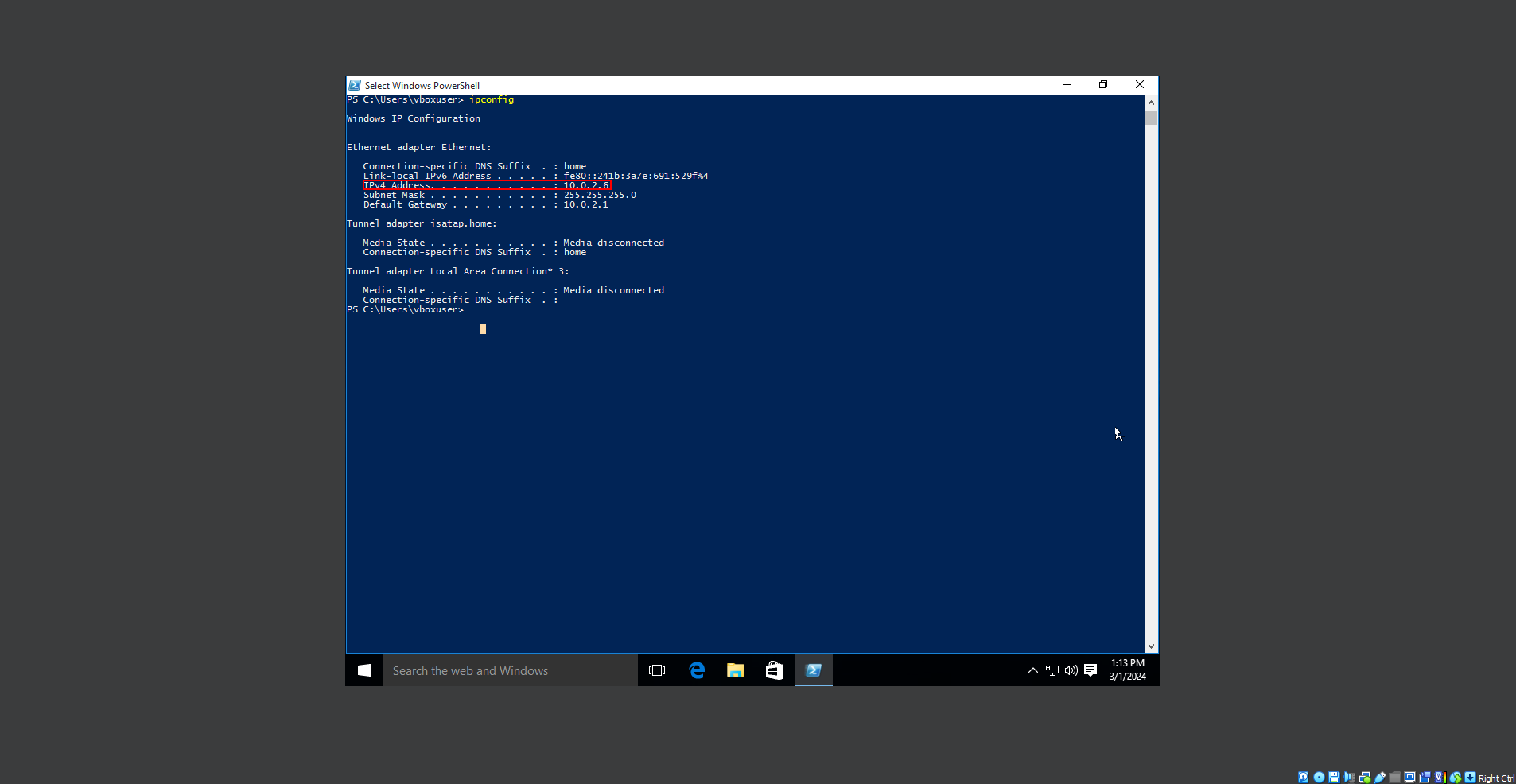 fore beginning this demonstration please note that this is for educational purposes and is simulated on an environment I personally own. I do not endorse unethical hacking or tampering with networks that do not belong to you. We will first spin up the target machine and identify its IP address. We can see that the target is a windows machine and its IP is 10.0.2.6.
fore beginning this demonstration please note that this is for educational purposes and is simulated on an environment I personally own. I do not endorse unethical hacking or tampering with networks that do not belong to you. We will first spin up the target machine and identify its IP address. We can see that the target is a windows machine and its IP is 10.0.2.6.
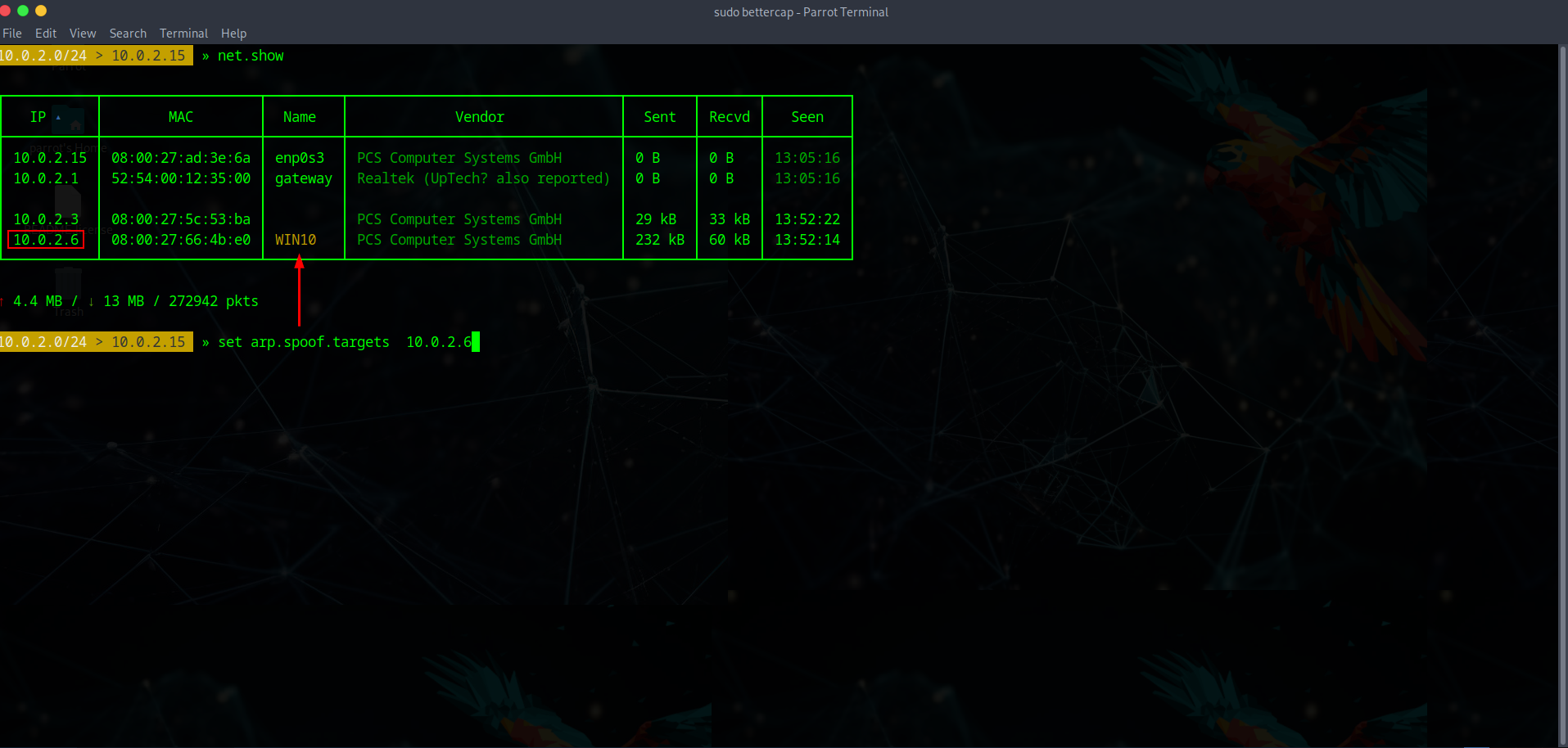
For the attacker to be able to monitor the traffic coming from the target machine, they first must connect to the same network and spoof the target machine into thinking that the attacker machine is the default gateway. By displaying the current un-altered arp table on a standard un encrypted connection, we can see that the Windows 10 target machine is displayed along with its IP address. The attacker can then select the target IP and begin injecting its ARP table.
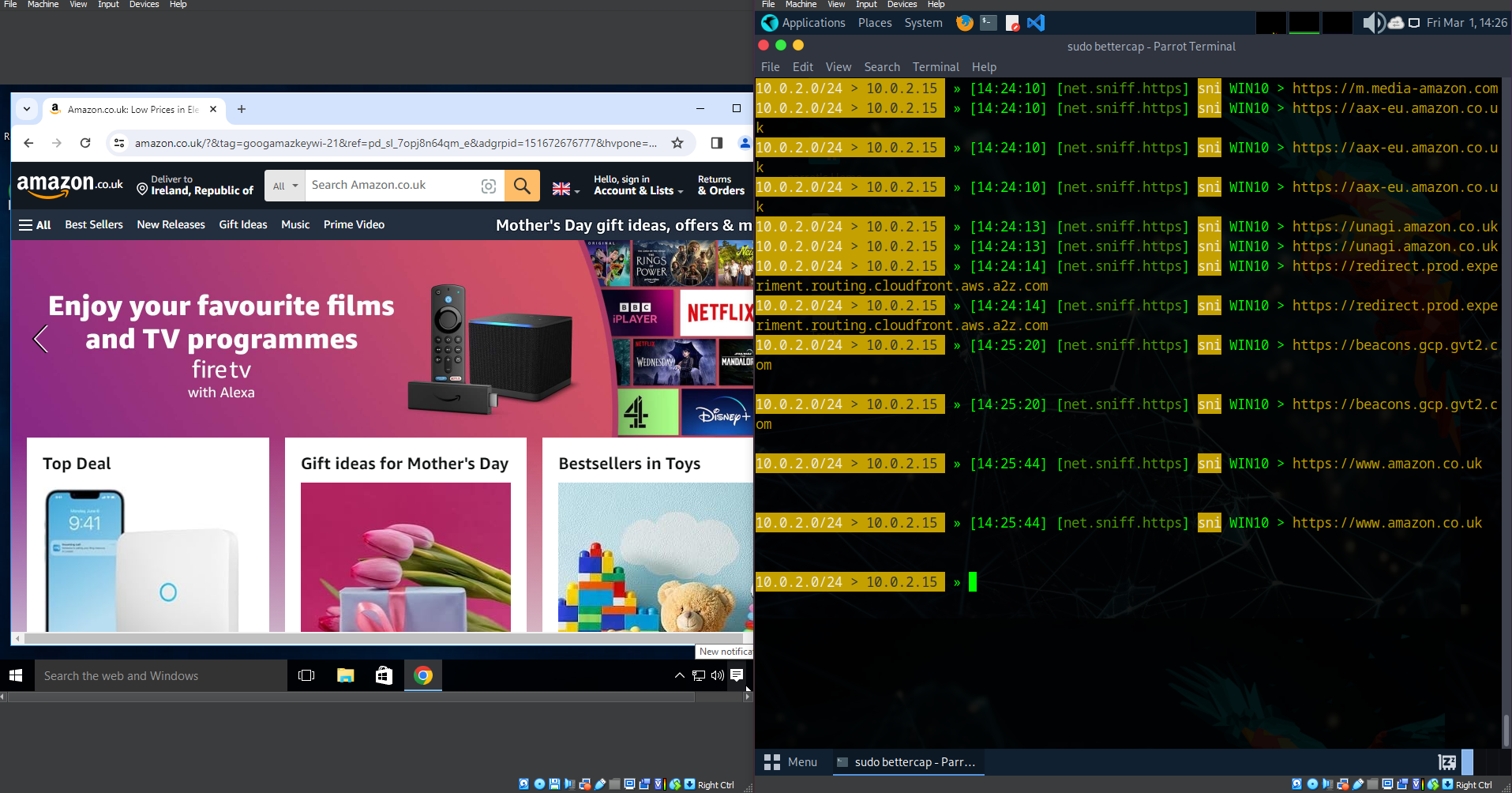
Once the Arp cache has been injected and poisoned by the attacker, they then can actively monitor all of the victims network traffic that is being diverted instead of it passing through the default gateway of the router.
How do I protect my systems from ARP spoofing?
Fortunately, you can implement a number of procedures and tools as part of your incident response plan to prevent ARP spoofing. A fairly simple way of protecting against ARP spoofing is to use packet-filtering firewalls and Encryption.
Packet-filtering firewalls flag data packets from an address that is found twice in the network, as this duplication suggests the presence of someone disguising themselves as another host. Encryption however, is probably the most important way to protect against an ARP attack. Due to the widespread use of encrypted communication protocols today, ARP hacking has become much more difficult. For example, most website traffic is encrypted using HTTPS, which prevents the hacker from reading the messages after intercepting them. Thus, the most important way to mitigate such attacks is to avoid sending unencrypted data. Another encryption tool worth noting is a virtual private network (VPN). When connected to a VPN, all your data will enter through an encrypted tunnel.
Share this post: on Twitter on Facebook on Google+